General
In order to set up an alarm group, it must be assigned a name. This will be used later for devices or alarm messages, which is why it should be as unique and descriptive as possible. The position of the new alarm group in the system is determined by selecting the higher-level alarm group. To make the devices subordinate to this alarm group less conspicuous when armed, stealth mode can be activated, which switches off the LEDs (does not affect the Ethernet port). If an alarm group is a particularly sensitive area, it is possible to extend its signaling range to the entire system. In the event of an alarm, this would trigger the configured alarm on all devices in the system.
Notifications
If a warning or alarm occurs in an alarm group or a subordinate alarm group, the corresponding authorized users are notified via the configured channels. These settings can be configured separately for each alarm group or inherited from the higher-level alarm group. Only users to whom this alarm group has been assigned are notified. This setting must be made in the corresponding user accounts.
For each alarm type (armed-active, permanently active, fire, sabotage, system message), you can specify whether notifications should also be sent when a warning occurs. You can also decide whether the number of notifications of an alarm type should be limited per hour.
Arming
If an alarm group is armed, this activates the evaluation of armed-active alarms.
In the event that the secured area still needs to be left after arming, a delay can be configured so that arming is only carried out after the set time.
The length of the acoustic signaling during arming can be changed or completely deactivated if necessary.
In normal operation, pending alarms prevent an alarm group from being armed. This can be bypassed for external sensors using the “Always arm” button.
Automatic acknowledgement
If an alarm is triggered, a user must respond and acknowledge it by default. If an alarm is not acknowledged, it cannot be triggered again, which means that any alarms of the same type (e.g. temperature alarm) that occur more than once are not reported. Automatic acknowledgement prevents this by acknowledging all acknowledgeable alarms from devices in the alarm group at a set interval.
Alarm settings
If a device in the alarm group triggers an alarm, this is signaled acoustically via the buzzer.
If a secured area needs to be entered before it is disarmed, the pre-alarm can be activated. All devices in the alarm group that have a configured alarm delay of 5s or more now receive an acoustic signal that the alarm group must be disarmed.
For the various alarm types, you can configure how long an alarm should be signaled via the buzzer on the devices.
Sabotage report
To prevent device failures in the system, the behavior of the devices in an alarm group can be configured when a possible sabotage is detected.
The set times indicate how long a device can be unavailable before a tamper alarm is triggered.
Active power
An alarm group can display and record the total active power of all subordinate SmartPDUs and SmartMeters. This can be activated separately for the supply lines.
Apparent power
An alarm group can display and record the total apparent power of all subordinate SmartPDUs and SmartMeters. This can be activated separately for the supply lines.
Consumption
An alarm group can display and record the total consumption of all subordinate SmartPDUs and SmartMeters. This can be activated separately for the supply lines.
Power Usage Effectiveness
Power Usage Effectiveness (PUE) is a key value for the energy efficiency of a data center. It indicates the ratio between the total power consumption of the data center and the power consumption of the IT devices. The alarm group can display and record this value in the DetailView.
Sluice
An alarm group can act as a gateway to control the transition between adjacent alarm groups, e.g. to achieve separation.
An interlock offers the possibility of controlling and monitoring the movement of people between several alarm groups.
The prerequisite for this functionality is always a passageway between the interlock and the adjacent alarm groups. This is used to detect external and internal doors of the interlock.
An external sensor can also be used to activate a presence detector, which can determine whether a person is inside the interlock area independently of the bookings at the DoorLocks. If no presence detector is active, the occupancy of the interlock is tracked via the bookings.
Example
Structure
There are two alarm groups (A, B) and between them the alarm group S, in which the interlock function has been activated. Each of these alarm groups contains DoorLocks that have been connected to form passageways:
- Passage A-S
- The DoorLock in A is an outer door of the lock
- The DoorLock in S is an inner door of the lock
- Passage S-B
- The DoorLock in S is an inner door of the lock
- The DoorLock in B is an outer door of the lock
In addition, an external sensor is configured in S, which acts as a presence detector.
Procedure
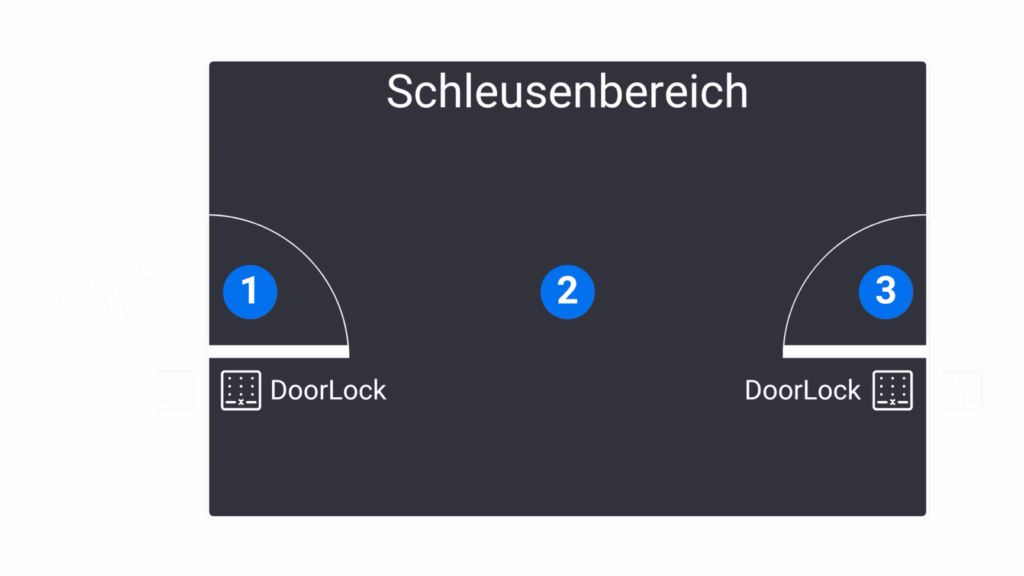
- A person wants to enter the lock area from A and books at the corresponding DoorLock.
- If there is no other person in the interlock area (presence detector) and all passages are closed (door contacts), access is granted and the person can enter the interlock.
- If the person is inside the airlock, all passages must be closed.
- The person books at the corresponding inner door of the passageway to B.
- If they have the appropriate access authorization, the door is opened and the person can leave the interlock again.
Anti-passback
If area change detection has been activated in the KentixONE system, alarm groups can be provided with extended functions.
Passages can be used to track which area (alarm group) a person last entered or left. If no more people are registered in an alarm group, it can be automatically re-armed.
DoorLock
A DoorLock can be assigned to an alarm group. This DoorLock is displayed in the KentixONE apps as quick access for the alarm group.
External alarm system
An alarm group in KentixONE can map the monitored area of an external alarm system.
The external sensors and switching outputs of the KIO7052 and KIO7060 expansion modules can be used to connect the return channel, the switching readiness (optional) and the switching signal of the external alarm system to KentixONE.
Event profile (automatic arming/disarming)
To automatically arm and disarm an alarm group, a previously created event profile can be assigned to it. This defines the times at which the alarm group is to be armed and disarmed.
Webhooks
Webhooks in KentixONE offer the option of sending an HTTP request to an external server when an event occurs. Each webhook can be assigned the types of alarms or warnings for which it should be sent.
Alarm groups support the following events:
| Name | Description |
| All alarms | The webhook is sent each time an alarm occurs. |
| Set-active alarms | If an active alarm occurs, the webhook is sent. |
| Continuous active alarms | If an active alarm occurs, the webhook is sent. |
| Fire alarms | If a fire alarm occurs, the webhook is sent. |
| Sabotage alarms | If a sabotage alarm occurs, the webhook is sent. |
| Changing the switching status (arming or disarming) | When the alarm group is switched, the webhook is sent. |
| Cyclical (5 min, 10 min, 15 min, 30 min) | The webhook is sent cyclically. |