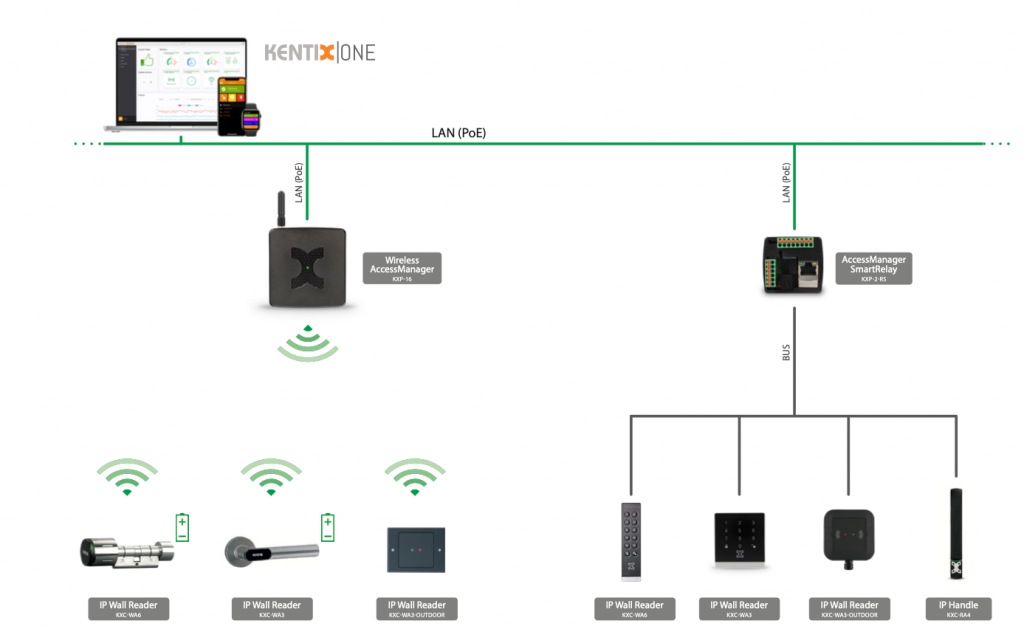
System topology of an access control system as an example
The requirement
Access control in companies and organizations has multiple challenges. On the one hand, an appropriate level of protection must be established in the area of access management in accordance with legal and organizational requirements; on the other hand, efficient and resource-saving operation of the locking system incl. the access control system must be ensured. The entire authorization management is essential.
In order to meet these challenges, controlled, electronic access via RFID transponder and/or PIN code is included. Establish real-time documentation of access and door status. The management of the entire system and all authorizations should be as automated as possible from a central location. All system states (open doors, etc.) should be clearly monitored in a dashboard from any location and undesired states should be alerted.
Installation and operation should be cost-effective and simple. Open interfaces should enable easy integration into third-party systems. Free scalability, modularity and cost-effective, simple maintenance must be part of the solution concept.
The Kentix system solution
Access control is handled by the Kentix online IP access control system, in which each individual locking point is always online and is managed centrally in real time via a web interface, among other things. IP wall readers with RFID and PIN code readers (also 2FA) are used at the electromechanical access points (doors, gates, barriers, etc.), two of which are connected to a SmartRelay module. The SmartRelay module provides the power from its integrated PoE splitter that is required to open a lock when an authorized booking is made. In addition, door contacts are connected to the smart relay module to permanently monitor the status of the doors.
Doors to and in the building are equipped with the Kentix radio knob or the Kentix radio lever handle, depending on the application. The radio locking units are connected via the Kentix AccessManager. Thanks to unlimited networking of Access Manager and SmartRelay modules, the system is freely scalable across locations. Alarm zones can be set up at any access point by authorized persons, incl. the user. Verification of constraint, arming and disarming.
Via an integrated web server application and/or open interfaces (LDAP, ReST-API, etc.), the system can be managed automatically from a central location in real time and authorizations can be granted or revoked. Furthermore, the system documents or, if necessary, alerts who has gained access, when and where. Remote opening of doors is also possible through the integrated software.
The simple, contemporary and resource-saving operation is realized by the KentixOS. The KentixOS is the integrated, freely scalable and modular IoT software platform that provides open interfaces for easy integration with third-party systems (ReST-API, WebHooks, SNMP, LDAP, etc.) in addition to web front-ends. At the same time, the KentixOS is the basis for more advanced AI analyses and visualizations.
